Conditional Access can now require reauthentication every time!
I stumble across this new feature when doing a monthly review of CA rules. Users with admin roles had a session requirement for Sign-in Frequency to reauthenticate every day. But hey, there´s a new setting in here now: “Every Time”. This setting makes sense. Then you need to reauthenticate every time you start something new. This feature is in preview so you are limited to a few specific use cases:
- Require user reauthentication during Intune device enrollment, regardless of their current MFA status.
- Require user reauthentication for risky users with the require password change grant control.
- Require user reauthentication for risky sign-ins with the require multi-factor authentication grant control.
Lets see how it looks like:
- Go to Azure Active Directory in the Azure portal
- Select Security
- Select Conditional Access
- Click New Policy and select Create new policy
- Enter a suitable name for your new policy
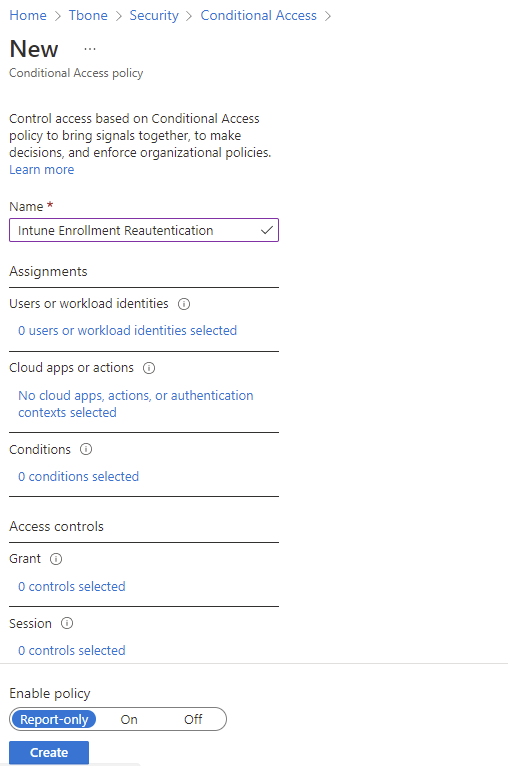
- Select to Target all users or your pilot group
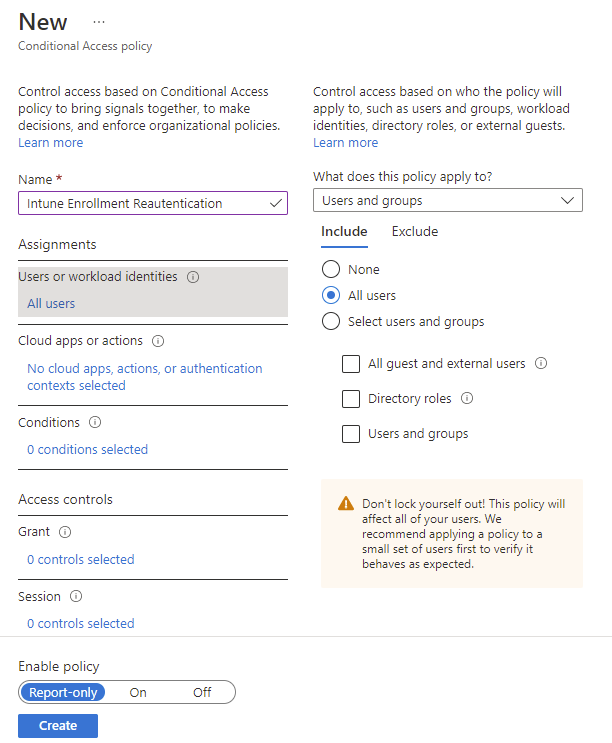
- Select a specific app “Microsoft Intune Enrollment”
It does not work with the “user action – register or join devices”. In preview its only enabled for the specific Microsoft Intune enrollment app.
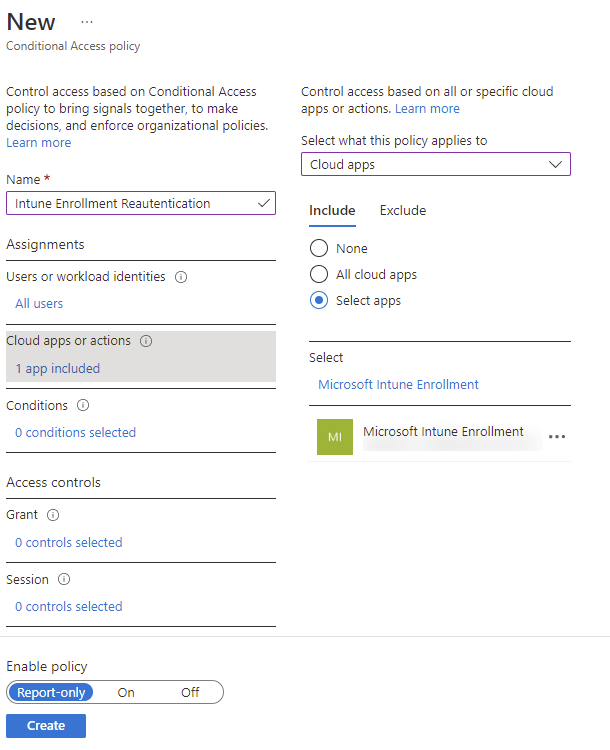
- If you need specific conditions and exclusions, time to add them now. But keep in mind, conditions are not required. It can be empty.
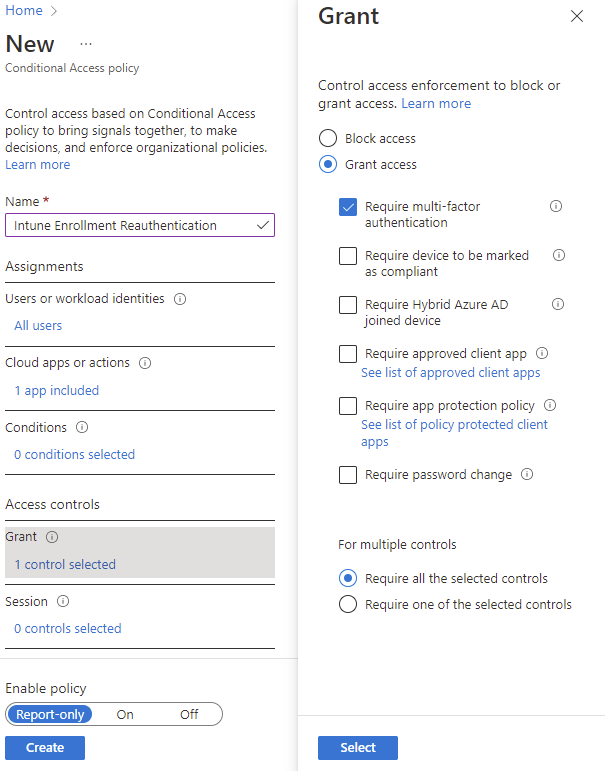
- Set the Grant control to Require Multi-Factor Authentication
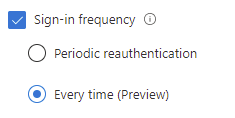
- And finally, in Session select Sign-in frequency and select Every Time(Preview)
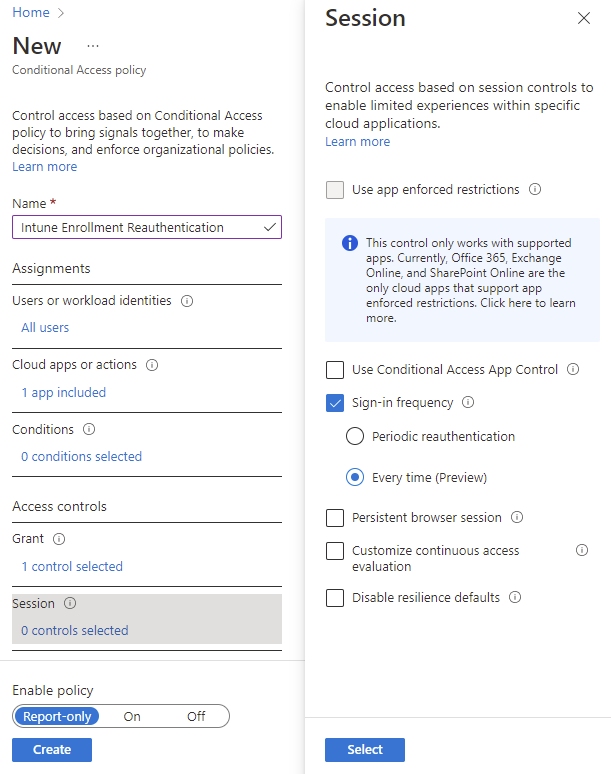
That’s it! Now your users will be reauthenticated every time they try to enroll their device, even if they have tried before. There has been some incidents with emulating devices and the enrollment process to gain access to company data. This will help eliminate these kinds of attacks.