Passwordless Onboarding with Autopilot

I just came home from Workplace Ninja UK Conference. This is a wrap-up of my session.
Embracing the Future
In the ever-evolving landscape of digital security, the move towards a Passwordless environment is not just a trend, it’s a necessity. With Intune Autopilot, a secure, user-friendly onboarding is simple to implement. Let’s dive in and look at the different Passwordless methods that works together with Autopilot..
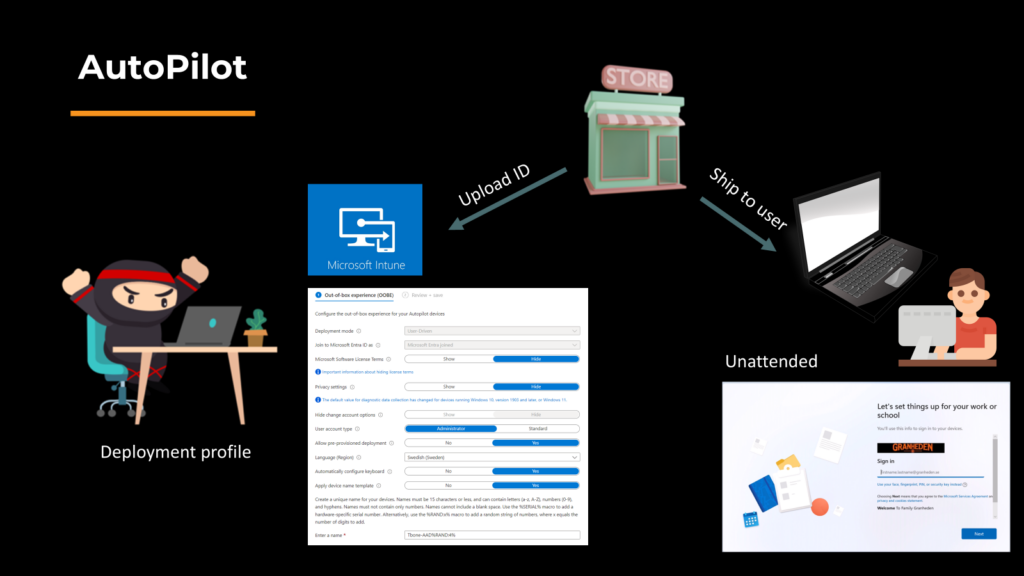
What is Autopilot?
Autopilot is a feature in Microsoft Intune, designed to automate the device deployment process. It simplifies the setup of new devices, making it seamless for IT administrators to ship devices directly to users. With Autopilot, devices are pre-configured with deployment profiles, ensuring an unattended and consistent setup experience. I will not go deeper than that in this blog.
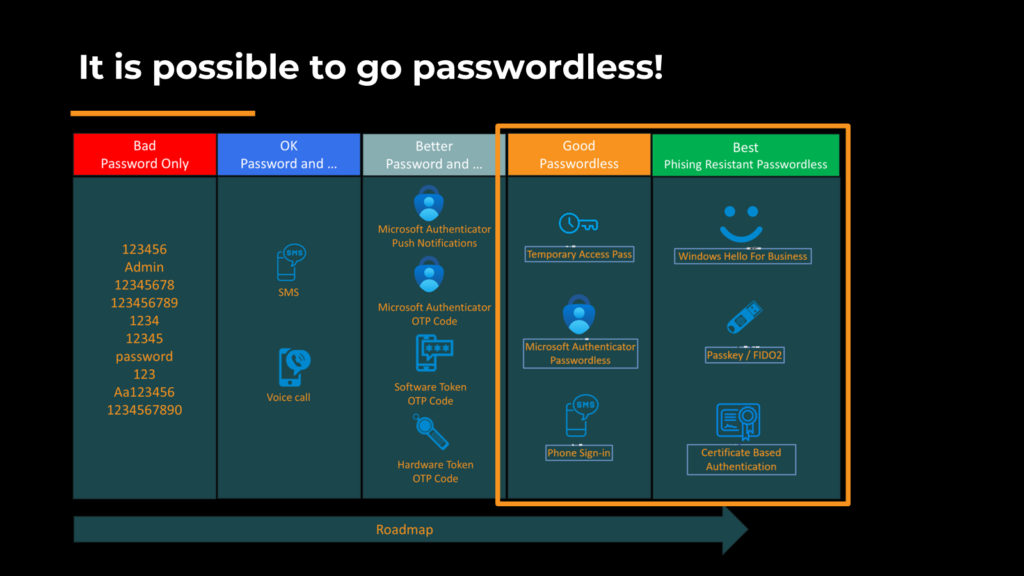
Why Passwordless?
The traditional password system is fraught with vulnerabilities. Passwords can be easily reused, guessed, hacked, or even eavesdropped upon. They are often the weakest link in our security chain, leading to a plethora of risks. Even if we protect cloud services with Conditional Access and require MFA, this doesn´t cover our local network services. They are still vulnerable and can be accessed directly with username and password.

Going Passwordless is possible and simple! Users hate passwords and password changes. If you implement Passwordless you will be the hero! Users love it and you will raise the security boundary. In Entra we we have at the moment 6 different Passwordless methods.
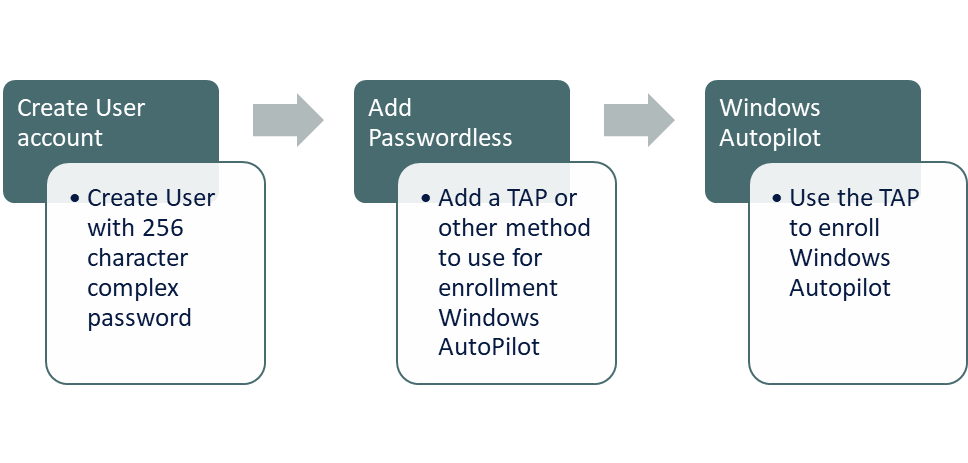
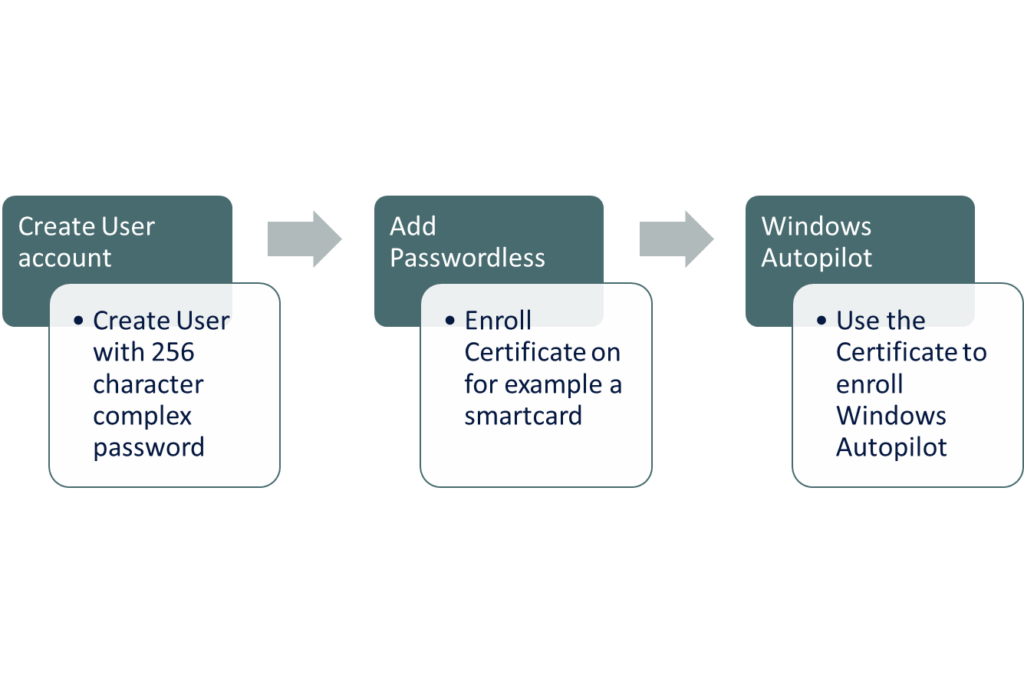
Onboarding New Users with Passwordless and Autopilot
The onboarding process using Passwordless and Autopilot involves a few key steps:
- Create a User Account: Start by creating a user account with a complex 256 character password that won’t be used by the user.
- Issue a Temporary Access Pass (TAP): Instead of giving the password to the user, we hand out a time limited access pass to only use for onboarding.
- Add Passwordless Methods(Optional): Use the TAP to enroll a Passwordless method. For example a WHFB or FIDO2 key.
- Run Autopilot with Passwordless: Use Passwordless method to install and configure the Windows device.
Passwordless methods and autopilot
Temporary Access Pass (TAP)
A time-limited passcode that allows users to set up or onboard devices or recover their authentication methods, especially useful when they don’t have access to their authentication devices. It’s a one-time or time limited use passcode.
Temporary access pass is a very simple Passwordless onboarding with autopilot:
Windows Hello for Business
As you can see in the video for Temporary Access Pass enrollment, it ends with the configuration of Windows Hello For Business. So the Temporary Access Pass is temporary used to enroll and another Passwordless method. Windows Hello for business is a very secure, and user-friendly way to log in to Windows devices using a PIN, facial recognition, or fingerprint. It replaces passwords with strong two-factor authentication.
We cannot use Windows Hello For Business at first login in Autopilot, so we are dependent on a second Passwordless method that we can use initially.
Microsoft Authenticator
Most users also have a mobile phone. Microsoft Authenticator can be configured for Passwordless sign in. It’s commonly used for multi-factor authentication (MFA), but needs to be configured to be Passwordless. If the user enable Passwordless it will add an additional layer of security when the password can be 256 characters and complex.
When using Microsoft authenticator with password. the password is a factor to verify user identity. As you can see we have at least 4 factors when using this method.
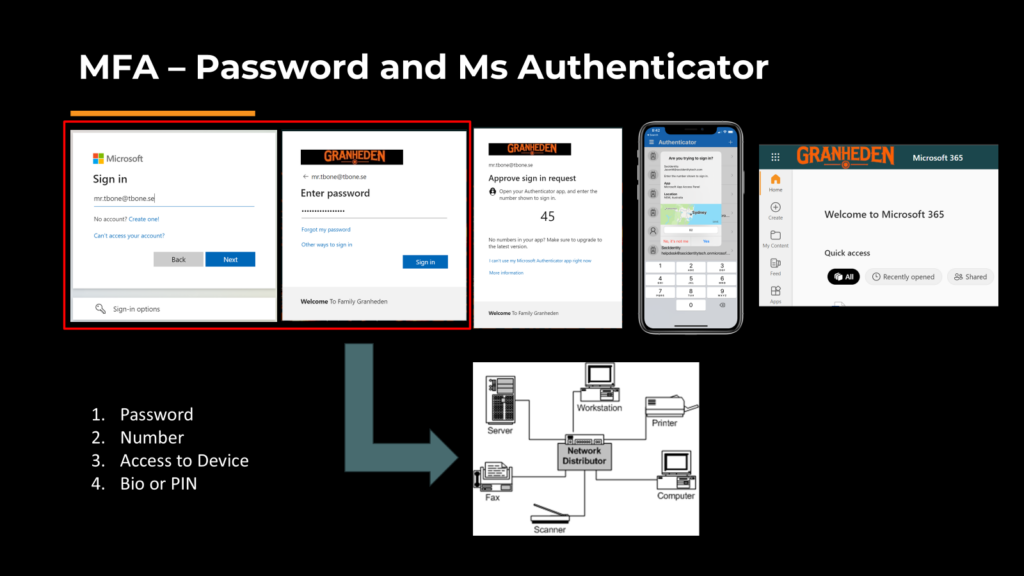
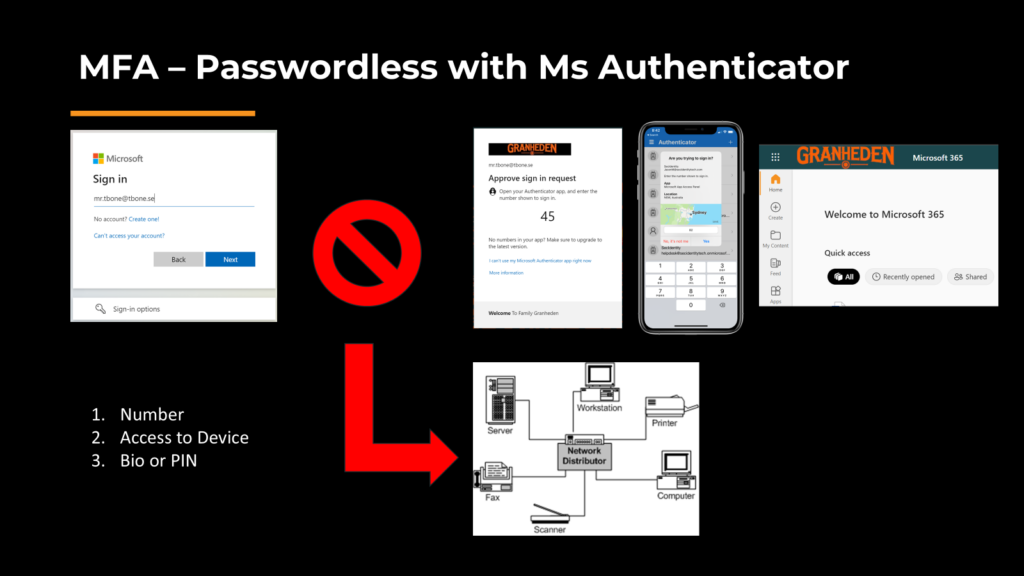
But if the password is known and can be stolen, it can be used on other services on your LAN for example. If you instead configure Passwordless, we simply remove the password from the process. But we still have 3 factors. Due to the security risk with password, this is better then having the password as a factor.
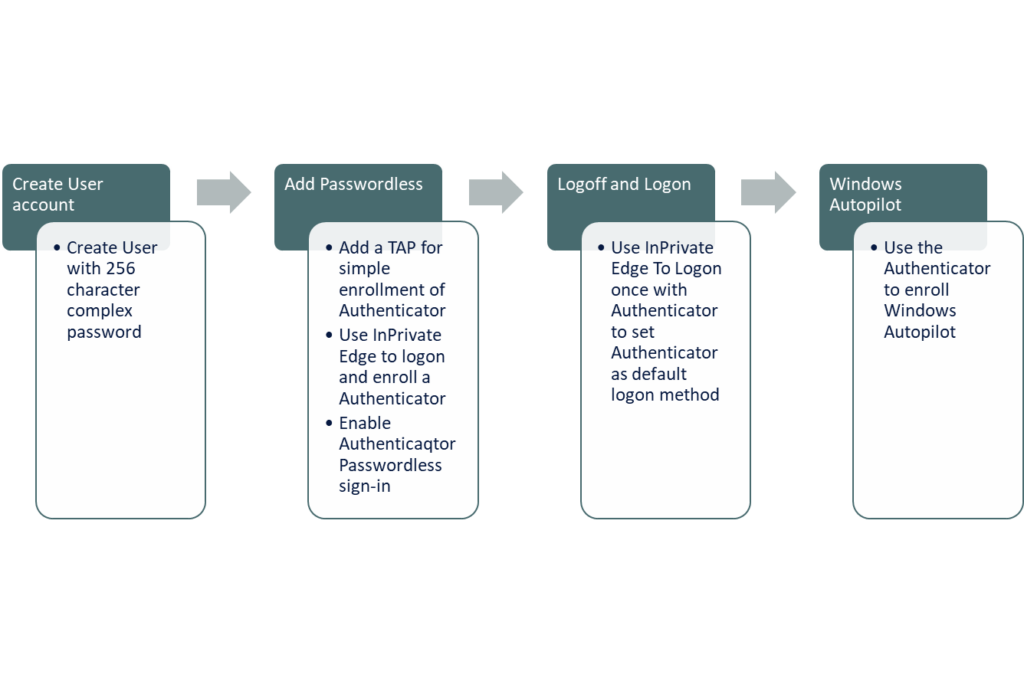
We can use Microsoft Authenticator to onboard with autopilot. the onboarding process often needs to be combined with a Temporary Access Pass to register the Microsoft Authenticator app. A trick is then to logoff and logon once to set the method as the default method for the user.
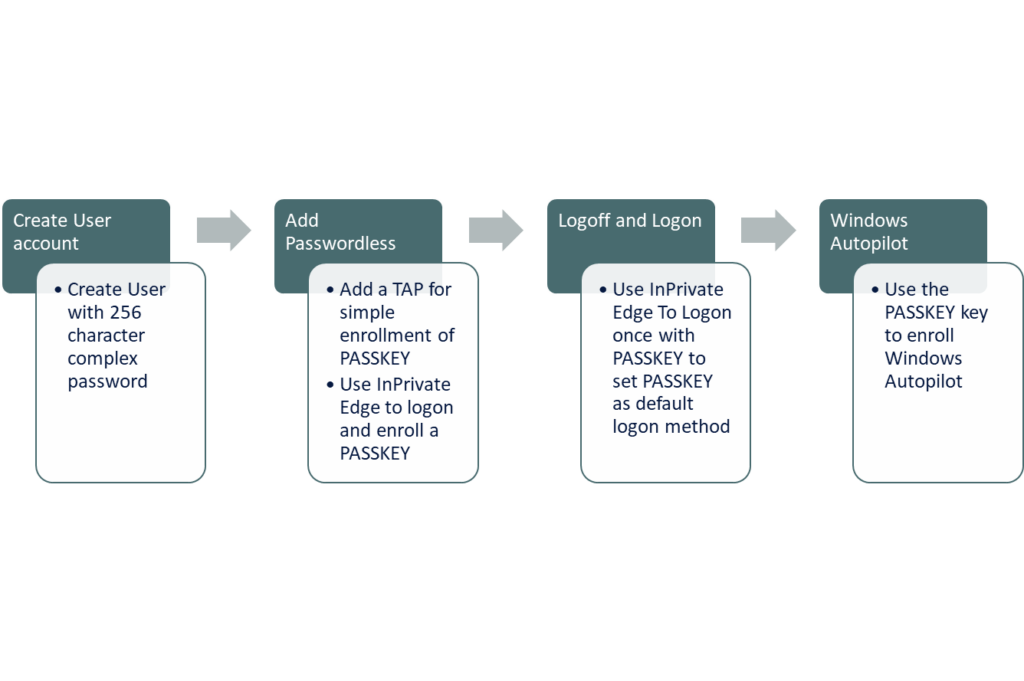
Passkeys and FIDO2
FIDO2 keys has is a physical key you insert in the USB port to verify your identity. Passkeys are a new type of FIDO2 enabling users to use their phones to store the credentials. Both uses FIDO2 technology. Passkeys in Microsoft Authenticator is still in preview and should not be used in production yet.
We can use FIDO2 security keys when onboarding with autopilot. This will also often require a Temporary Access Pass for the initial enrollment for the FIDO2 key.
Certificate Based Authentication
Utilizes digital certificates to verify a user’s identity, allowing for secure access to networks and services without the need for a password. It’s part of a public key infrastructure (PKI) and often used in combination with smart cards but can also be stored on many FIDO2 security keys to plugin as act as a virtual smart card.
Certificate Based Authentication works with autopilot and the onboarding process is often admin driven to enroll a smartcard to the user.
Phone Number Sign-in
This is a quite new form of authentication where a user can sign in using their phone number instead of a username. A verification code is sent to the phone, which the user enters to gain access. It’s a convenient option for users who prefer not to remember usernames.
It is actually the old SMS multifactor authentication where we simply skip the password. You would normally enter username, enter password and get an SMS code to enter. With Phone Number sign in we skip the password and enter our phone number as username, get an SMS code to enter.
This is a week method. But way better than passwords! This could for example be a replacement for using Temporary access pass in the initial enrollment of other Passwordless methods. The new user get their phone at the first day at work and can enroll Passwordless by receiving the SMS code.
Phone Number Sign-in does not work with Autopilot. The first logon prompt does not support this method:
Implementing Passwordless with Autopilot
To successfully implement a Passwordless system with Autopilot, planning is crucial. But there is also some configuration needed to get the process working in different scenarios. Autopilot and deployments often have glitches and bugs that interfere with the process.
Go Cloud Only
The Passwordless methods works best if you have a cloud only Windows. This is a Windows only joined to Entra ID and not your local domain. Most companies still join their Windows to Local AD and get a hybrid join, joined both to AD and Entra ID. This is so unnecessary! Most things work today even if the computer is Cloud only joined, if you enable Kerberos Cloud Trust.
Kerberos Cloud trust enables the Entra ID to issues Kerberos user tickets, accepted by the local AD, to the cloud only joined computer user. So, if logging on with Windows Hello For Business, you can access all Kerberos protected resources and services on LAN. How about NTLM and basic auth? GET rid of them, they won´t work!!!!!
More info on how to enable Kerberos Cloud Trust
Unexpected Shutdowns
When running Autopilot, it is optimized to do a unattended installation without any unexpected actions. If nothing interferes with the installation, the user only sign in once and the access token is preserved during the whole process. At the and the access token is used to configure Windows Hello For Business.
But sometimes we have unexpected shutdowns. This is a known bug and Microsoft is working on different solutions. But in my opinion, you should be prepared for this. Update your guides and inform users that they might get 2 logins before desktop appear. completions.
Unexpected shutdown can occur if you assign these policies to devices:
- Update Rings
- Security Baselines
- Device Controls
A workaround is to assign them to Users instead. Then those will work better in Autopilot.
Windows Web Sign-in
A better bullet proof workaround to the unexpected shutdowns is to prepare for them and enable Windows Web Sign-in. The Windows Sign-in normally just show Password and Passkey login, with no possibility to login with Temporary Access Pass. If you enable Windows Web Sign-in, you also get a possibility to login with a web-based sign- using your Temporary Access Pass for example.
Enable the web sign-in with an Intune Configuration policy in settings catalog.
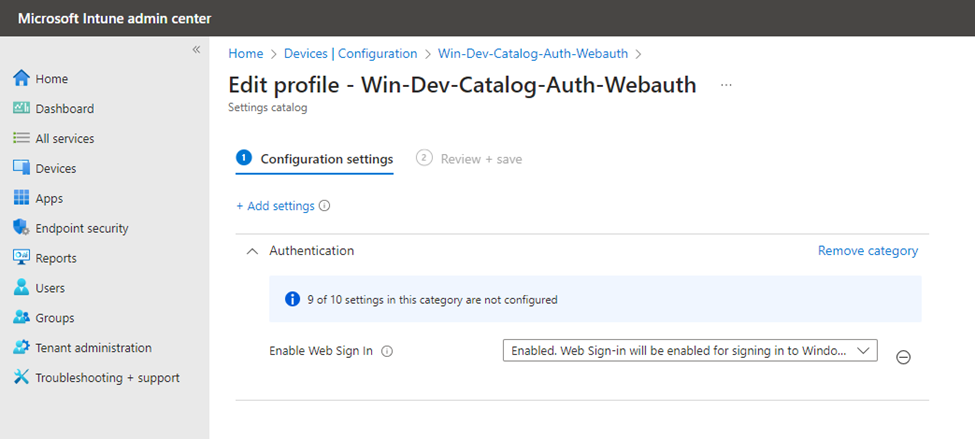
If you need to exit web sign-in and go back to the normal sign-in, press CTRL+ALT+DEL
Windows Passwordless Experience
If you implement Passwordless in your environment, why not remove the password from the Windows sign-in. Then people must use a Passworless sign-in.
You can the enable a feature called Passwordless Experience, also in Intune settings catalog:
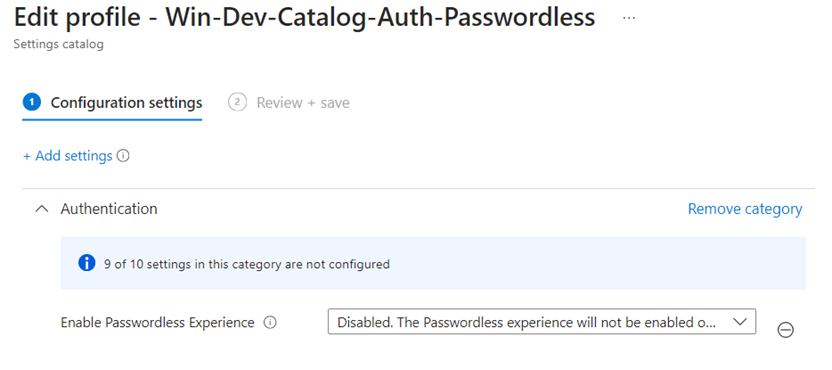
If you need to use Password in when this is enabled, you can choose “Other User” and then it gives you a full set of login methods.
Conditional Access
To prevent users from using password at Autopilot enrollment, we can use Conditional Access rules.
I normally exclude the service “Microsoft Intune Enrollment” from the default baselines requiring MFA on all services. I also recommend to require specific MFA methods and only include Passwordless methods. You can also exclude Temporary Access Pass in that policy and only allow that to be used for Intune enrollments.
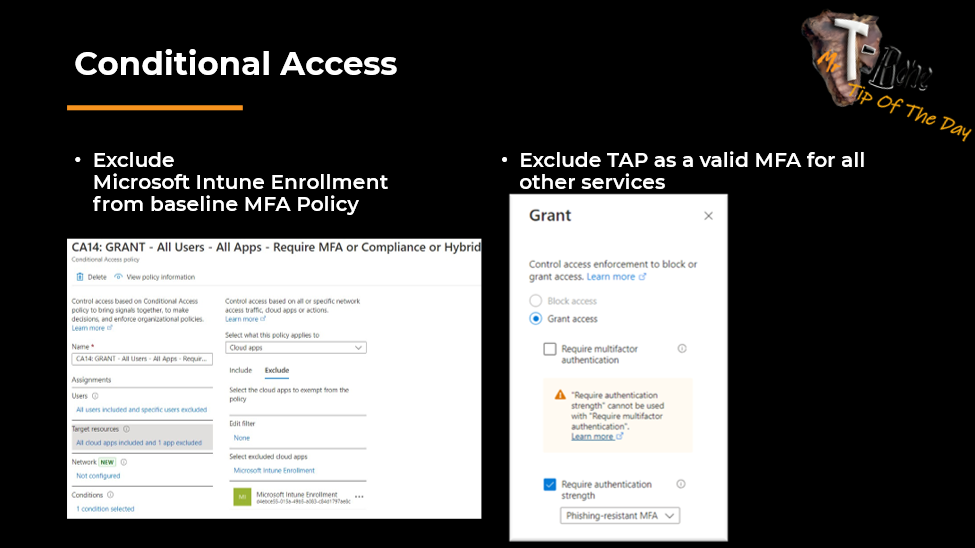
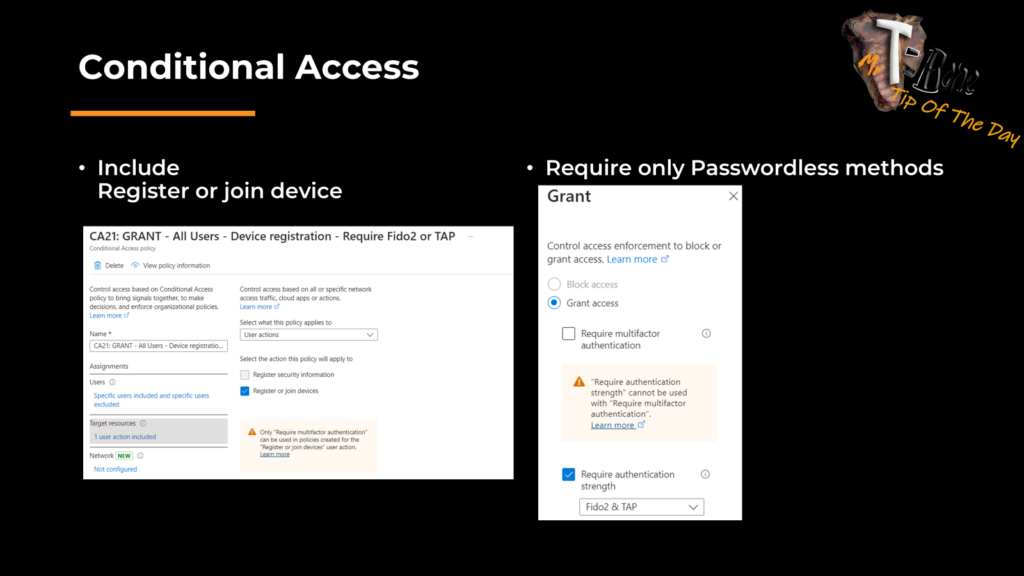
Then I add a separate Conditional Access policy for the action “Register or join device” that require and allow for example only Temporary Access Pass.
Conclusion
The shift to Passwordless onboarding with Autopilot represents a significant leap forward in both security and user experience. By embracing these technologies, organizations can protect their assets more effectively while providing a smooth onboarding process for their users. It’s time to leave passwords in the past and move forward with confidence into a Passwordless future
Today, most of my customers use the Temporary Access Pass to onboard new users. The Temporary access pass is used to enroll Windows Autopilot and ends up with the phishing resistant and secure Windows Hello For Business. A very simple enrollment for the end user. I really like this process.
Some of my customers also go for FIDO2 Passkeys. They onboard users by admin enroll the FIDO2 passkey by opening an InPrivate browser and login as the user with a temporary access pass. Then they hand over the FIIDO2 Passkey to the user. It can of course be user driven, but most my customers what’s control of the enrollment
Prepare for multiple device users
Don´t forget that most users also have a mobile phone and other devices to onboard. In this case the Temporary Access Pass can be used for them all to do the initial enrollment. But the device should then, just like windows, enroll a more secure and long lasting Passwordless method. The most common one is the Ms Authenticator. Remember to also include to enable Passwordless in the guide. This is a manual step the user must take.