ZeroTrust Network Access with Microsoft Entra Global Secure Access
Introduction
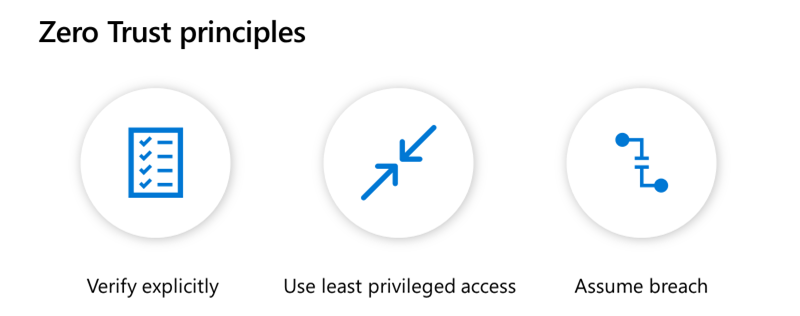
In today’s world, where remote work is becoming the norm, network security is more important than ever. Traditional VPN solutions are not enough to protect enterprise resources from cyber threats, as they often provide a false sense of security, require complex management, and create a frustrating user experience. Moreover, VPNs are not compliant with the Zero Trust security model, which is based on three principles:
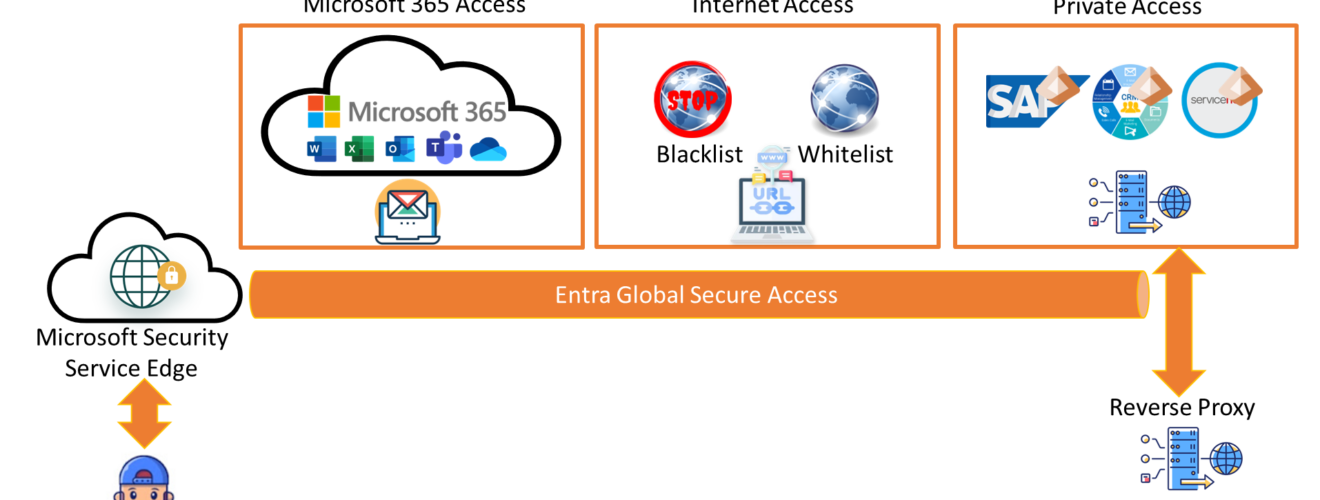
That’s why Microsoft has introduced Entra Global Secure Access, a cloud-native network access solution that provides secure, seamless, and easy access to enterprise resources from any location. Entra Global Secure Access is compliant with the Zero Trust security model, providing a superior solution to traditional VPNs. In this blog post, we will explore how Entra Global Secure Access works, what benefits it offers, and how it works.
Entra Global Secure Access Traffic Profiles
Entra Global Secure Access provides various secure access profiles, including Microsoft 365 Access Profile, Private Access Profile, and Internet Access Profile, to enable secure access to different types of resources. Each traffic profile has its own traffic policies and conditional access policies, which can be customized and assigned to users and groups. Let’s take a look at each traffic profile in more detail.
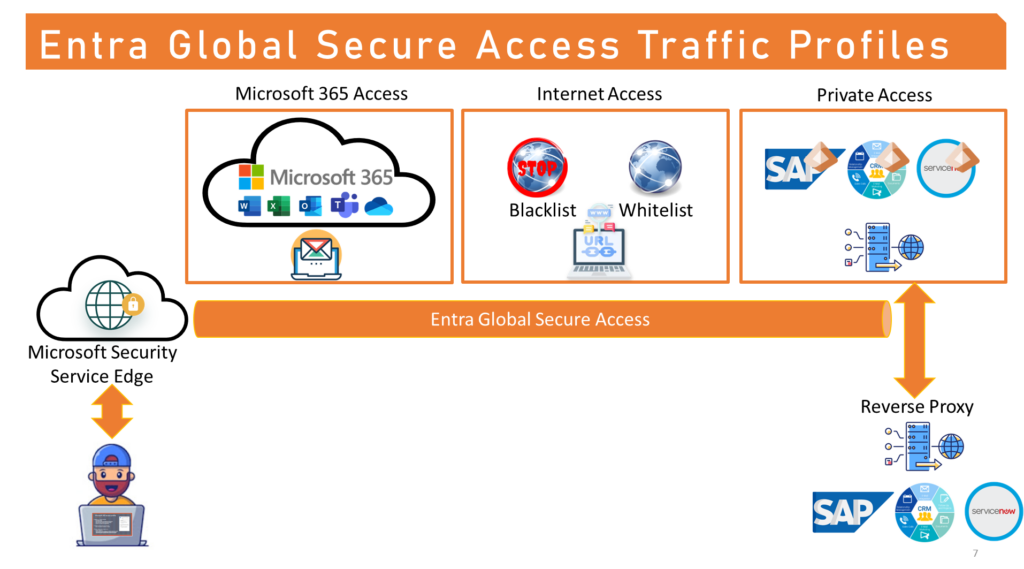
- Microsoft 365 Access Profile: This profile applies to traffic that is destined for Microsoft 365 services, such as Exchange Online, SharePoint Online, OneDrive for Business, and Microsoft 365 Common and Office Online. (Note that Teams is currently not supported). This profile allows you to use Entra Global Secure Access as a proxy for Microsoft 365 traffic, and apply conditional access policies to enforce security and compliance. For example, you can require multi-factor authentication, device compliance, or location-based access for Microsoft 365 traffic. You can also assign this profile to remote networks, so that the network traffic is forwarded to Entra Global Secure Access without having to install the client on end user devices.
- Internet Access Profile: This profile applies to all internet traffic except Microsoft 365 traffic. This profile allows you to use Entra Global Secure Access as a web gateway, and apply security profiles and conditional access policies to protect your users from malicious and inappropriate websites. For example, you can block access to certain categories of websites, such as gambling, adult, or social media, or require security profiles, such as the baseline or custom policies for internet access. You can also use continuous access evaluation to monitor and revoke access based on real-time signals.
- Private Access Profile: This profile applies to traffic that is destined for private or on-premises resources, such as servers, applications, or databases. This profile allows you to use Entra Global Secure Access as a reverse proxy, and provide granular access control and real-time protection for your private resources. For example, you can use Quick Access to access a single Entra Enterprise app, or use Enterprise Application to access multiple Entra Enterprise apps that are assigned to users. You can also specify the IP or FQDN and port of the private resources, and use Entra Global Secure Access connectors to establish a secure connection between your on-premises network and Entra Global Secure Access.
Entra Global Secure Access Requirements
To use Entra Global Secure Access, You only need a Microsoft Entra P1 license that also is included in Microsoft 365 F3 and E3. This makes this a very cheap solution compared to other vendors of ZTNA products. To use Entra Global Secure Access you need to meet the following requirements:
- License: You need to have a Microsoft Entra ID P1 license, and a Microsoft 365 F3 or E3 license is recommended.
- Client app
- Windows: You need to install the Global Secure Access Windows client on your Windows 10/11 x64 devices. The devices must be either Microsoft Entra joined or Microsoft Entra hybrid joined. Azure Virtual Desktop single-session and Windows 365 are supported, but Azure Virtual Desktop multi-session is not supported.
- Android: You need to install the Defender for Endpoint Android app on your Android 10 and later devices. The devices must be Microsoft Entra registered. Unmanaged devices must have the Microsoft Authenticator app, and managed devices must have the Company Portal app. Device enrollment is required for Intune device compliance.
- iOS & MacOS: These devices are currently in private preview.
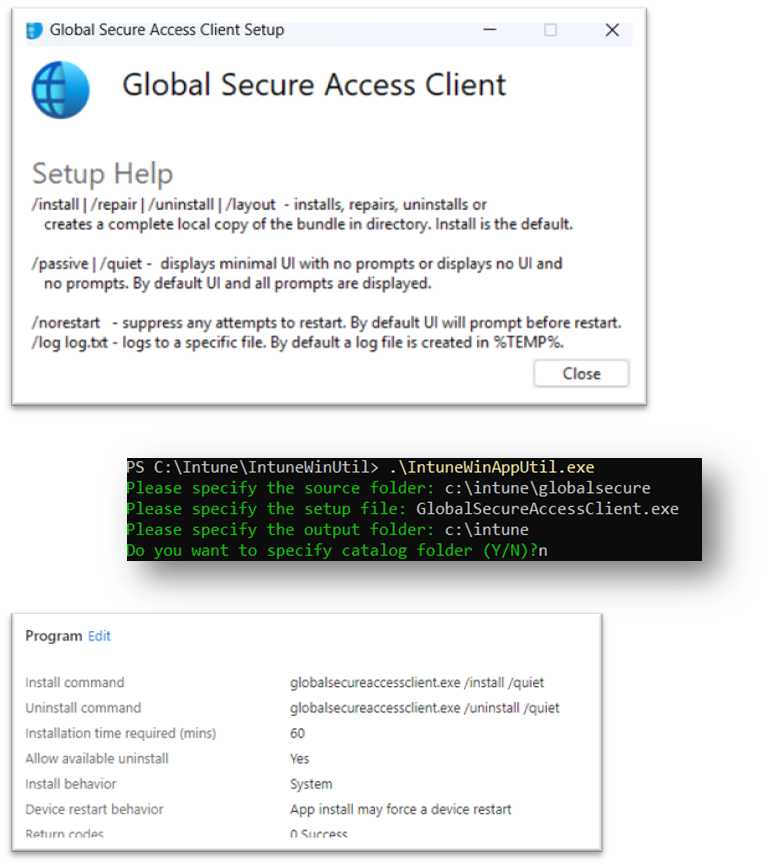
Deploy Global Secure Access Windows client with Intune
The client is simple to deploy with your favorite deployment tool. To deploy it with Microsoft Intune, just download the client from the Entra portal and package with Intunewinapputil. The installation syntax is shown in the images below.
Entra Global Secure Access Benefits
Entra Global Secure Access offers many benefits compared to traditional VPN solutions, such as:
- Cloud-Native: Entra Global Secure Access is a cloud-native network access solution that provides global scalability, reliability, and performance. You don’t need to install or maintain any on-premises infrastructure, and you can leverage the power of Microsoft cloud services.
- Superior Security: Entra Global Secure Access provides superior security compared to traditional VPN solutions, ensuring that enterprise resources remain secure and accessible only to authorized users. You don’t need to open any firewall ports, and you can use conditional access policies and security profiles to enforce security and compliance. You can also use real-time threat protection, detecting and blocking potential threats before they can cause harm, providing an additional layer of security.
- Seamless Access and Enhanced User Experience: Entra Global Secure Access provides seamless access to enterprise resources, eliminating the need for a VPN client and providing a user-friendly experience. Users can access the resources they need from any location, device, or network, without compromising security or performance. Entra Global Secure Access also enhances user productivity and satisfaction, reducing frustration and support cases.
- Granular Access Control and Real Time Protection: Entra Global Secure Access provides granular access control, allowing administrators to set access policies based on user roles and applications, improving security and reducing risk. Entra Global Secure Access also provides real-time protection, detecting and blocking potential threats before they can cause harm, providing an additional layer of security.
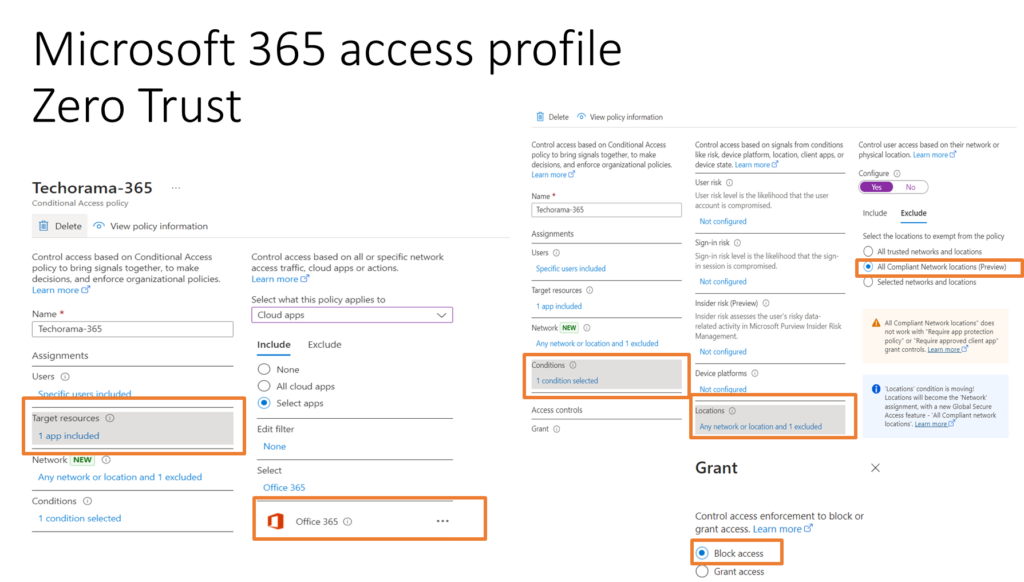
Zero trust example of
Entra Global Secure Access – Microsoft 365
With the Microsoft 365 traffic profile you can for example use Conditional Access to block all traffic towards Office 365 for all remote clients without the Global Secure Access Client Installed. If the Client is installed, it appear as comming from a “Compliant Network Location” and will be excluded from this blocking rule:
Zero trust example of
Entra Global Secure Access – Internet Access
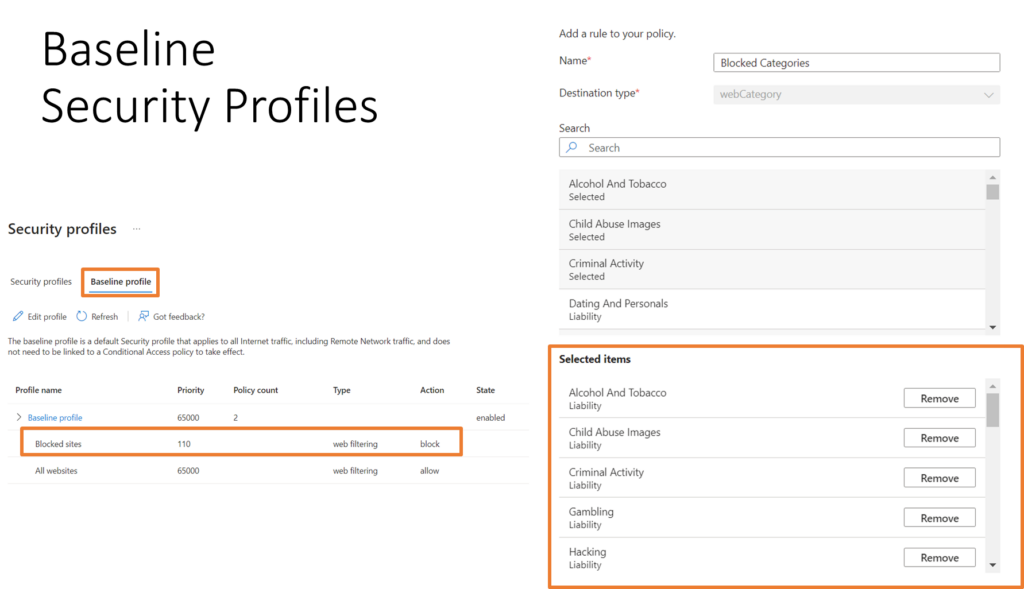
With Internet access, the rules are built with Security Profiles. In security profiles, you can allow or deny websites based on FQDN or web categories. These security profiles then need to be assigned to end users using conditional access. This is an example to block gaming and gambling sites for all users except for users assigned with a custom security profile:
Baseline to block all unwanted sites based on categories:
Custom Policy to allow gaming and Gambling sites:
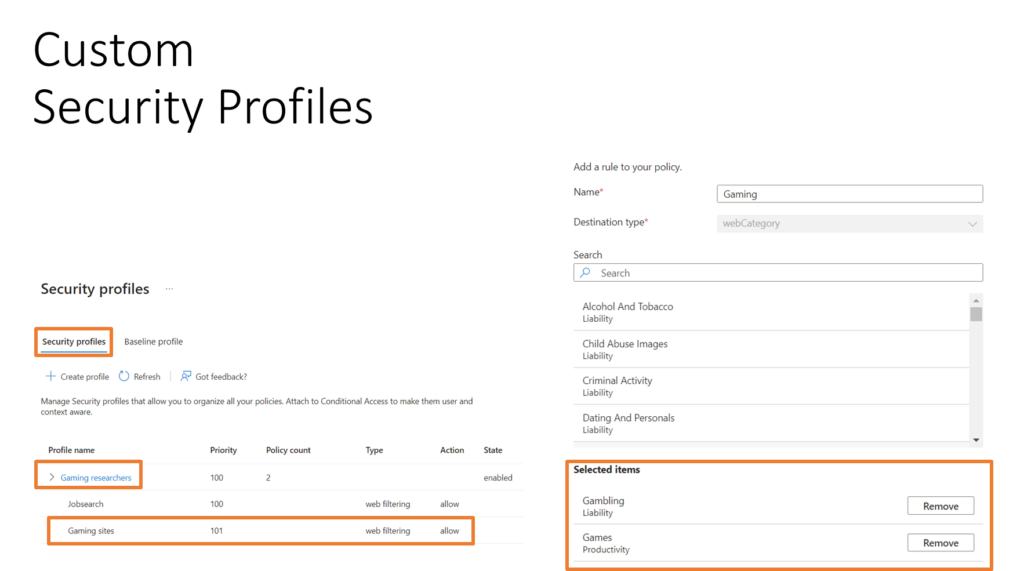
Assignment of the custom security profile to specific users with Conditional Access:
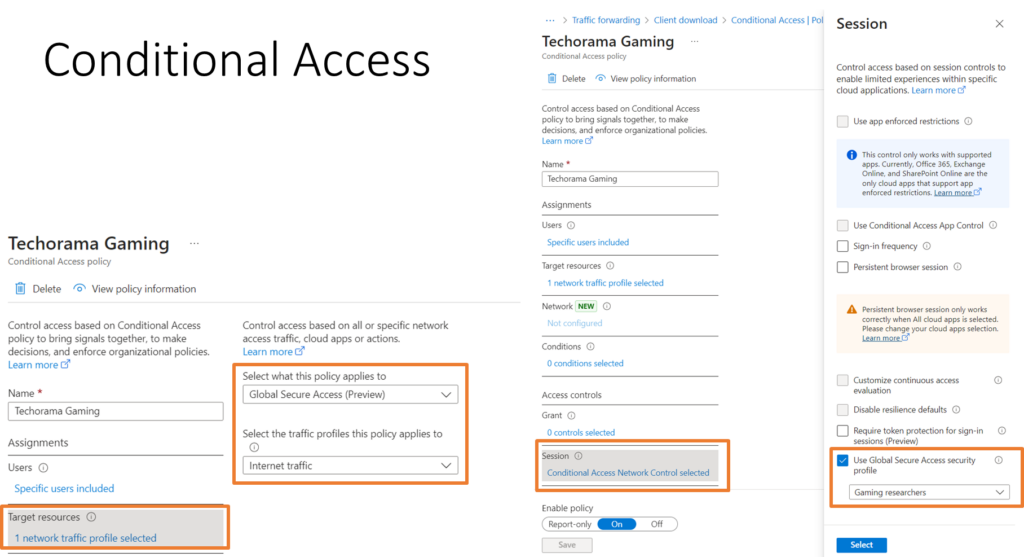
Zero trust example of
Entra Global Secure Access – Private Access
To access internal resources on your on-premises LAN, you need to install at least one Private Network Connector. It is basically a reverse proxy installed on an on-premises server. To achieve fault tolerance and load balancing, I suggest two or more servers for this. They can also be grouped if you for example have one application in Sweden and one in Canada. Then you can use the closest datacenter to access the application via reverse proxy.
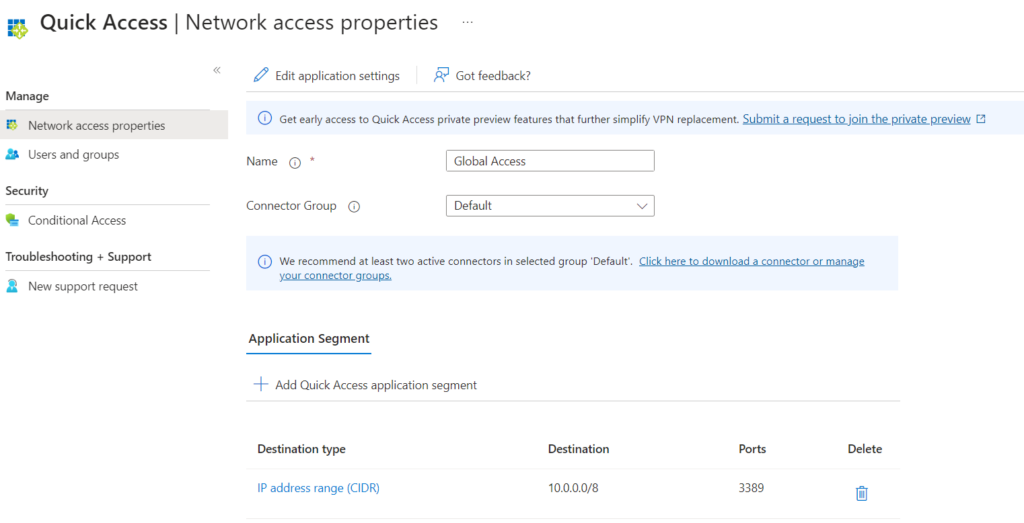
You the add a Quick Access rule or create a custom Enterprise app for your on-premise app network requirements. Quick Access is aimed as a default setting for a wide scope of users. Just add a rule and all connected users will be able to connect using that rule
Example of a Quick Access rule that allow RDP access to all servers on 10.0.0.0/8 network:
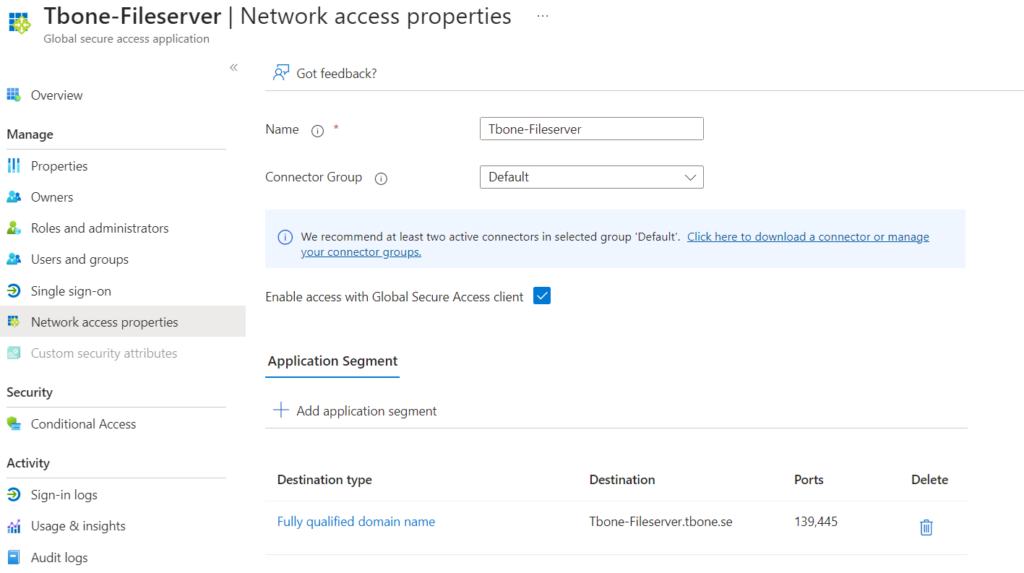
But to achieve least privilege, you should create custom Enterprise Apps for each app that you want to publish. Then you can assign each Enterprise app to specific users and only they can connect.
Example of an Enterprise App to allow fileserver access for specific users:
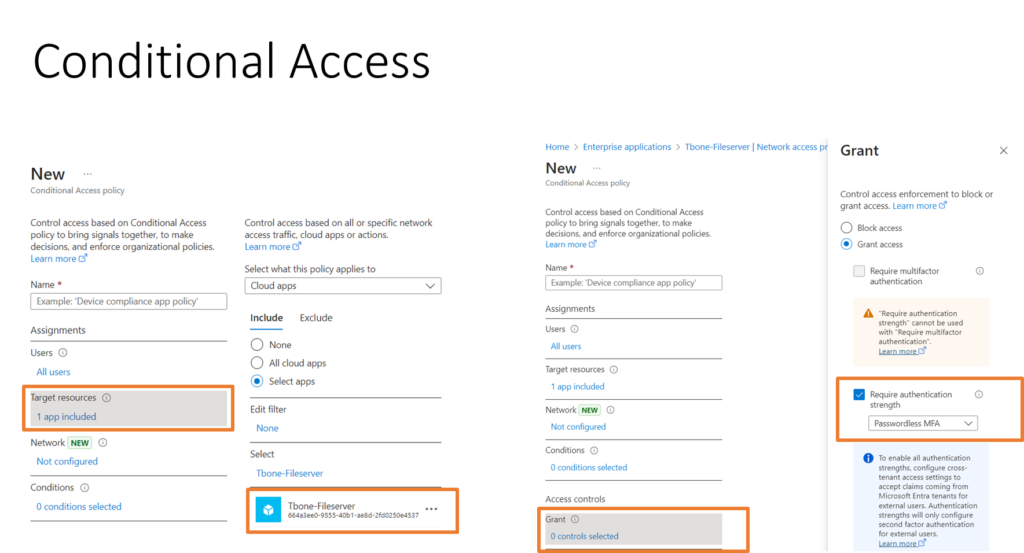
Finally you can use conditional access to specify specific requirements for your custom enterprise applications. Like requiring a passwordless authentication for fileserver access.
Conclusion
Entra Global Secure Access is a cloud-native, zero trust network access solution that provides secure, seamless, and easy access to enterprise resources from any location. Entra Global Secure Access offers many benefits compared to traditional VPN solutions, such as superior security, seamless access, enhanced user experience, granular access control, and real-time protection. Entra Global Secure Access also provides flexibility for different use cases, including Quick Access and Enterprise Application, to enable secure and seamless network access for enterprise resources.
There is a lot of glitches and lack of features now in the preview, but it is a preview. I hope and assume it will be awesome when going GA. If you want to learn more about Entra Global Secure Access, you can visit the official website. I hope you enjoyed this blog post, thank you for reading!