Create a Managed Identity to automate Intune tasks

When working with Microsoft 365, Azure and Intune, you sometimes need to automate things. To automate, you need some type of authentication. Credentials using old and unsecure passwords is no longer considered as safe, we need other secrets to provide authorized access. Service Principals was a first step to make the credentials more secure. But with Service Principals, you still use keys or certificates to verify the identity. This is where Managed Identities comes to a rescue.
With a Managed Identity you do not need to know any credentials at all, instead Azure manages everything. You just create it and it act as an Azure Application. You can assign permissions to that particular application, similar to assigning permissions to a real user.
Some of the benefits of using managed identities:
- You don’t need to manage credentials. The credentials are not accessible to you.
- You can use managed identities to authenticate to any resource that supports Microsoft Entra authentication, including your own applications.
- Managed identities can be used at no extra cost.
Select the managed identity type
A Managed Identity can be created in two different types:
System-assigned. Some Azure resources, such as virtual machines allow you to enable a managed identity directly on the resource. When you enable a system-assigned managed identity:
- A service principal of a special type is created in Microsoft Entra ID for the identity. The service principal is tied to the lifecycle of that Azure resource. When the Azure resource is deleted, Azure automatically deletes the service principal for you.
- By design, only that Azure resource can use this identity to request tokens from Microsoft Entra ID.
- You authorize the managed identity to have access to one or more services.
- The name of the system-assigned service principal is always the same as the name of the Azure resource it is created for. For a deployment slot, the name of its system-assigned identity is /slots/.
User-assigned. You may also create a managed identity as a standalone Azure resource. You can create a user-assigned managed identity and assign it to one or more Azure Resources. When you enable a user-assigned managed identity:
- A service principal of a special type is created in Microsoft Entra ID for the identity. The service principal is managed separately from the resources that use it.
- User-assigned identities can be used by multiple resources.
- You authorize the managed identity to have access to one or more services.
I prefer using System-assigned identities to secure the credentials when running Azure Automations.
Create a managed identity for Azure Automations
- Open Azure Portal
- Click Create a resource

- Search for and select create on Microsoft Azure Automation

- Put the Automation account in an existing or new resource group and give it a suitable name.

- Create the managed identity type

- Select if you should be able to connect to your automation account from public or private networks. Private is more secure but requires you to setup private endpoints.

- Tag the resource if you use tags, and select to create the automation account.

You now have an Azure Automation Account with a System-assigned Managed Identity

Assign Permissions to Managed Identity
To be able to connect and use services in Intune, we need to assign the managed identity permissons. This cannot be done in portal, you need to use PowerShell. This example uses the MG-Graph module.
<#PSScriptInfo
.SYNOPSIS
Script for setting permissions on Azure Automation Accounts
.DESCRIPTION
This script will assign specified permissions on an Azure Automation Account
.EXAMPLE
.\Set-MgAzureAutomationAccountPermissions.ps1
will assign specified permissions on an Azure Automation Account with settings in the modifyable region.
.NOTES
Written by Mr-Tbone (Tbone Granheden) Coligo AB
torbjorn.granheden@coligo.se
.VERSION
1.0
.RELEASENOTES
1.0 2024-01-04 Initial Build
.AUTHOR
Tbone Granheden
@MrTbone_se
.COMPANYNAME
Coligo AB
.GUID
00000000-0000-0000-0000-000000000000
.COPYRIGHT
Feel free to use this, But would be grateful if My name is mentioned in Notes
.CHANGELOG
1.0.2401.1 - Initial Version
#>
#region ---------------------------------------------------[Set script requirements]-----------------------------------------------
#endregion
#region ---------------------------------------------------[Script Parameters]-----------------------------------------------
#endregion
#region ---------------------------------------------------[Modifiable Parameters and defaults]------------------------------------
$TenantID = "d6f19297-08a2-4ade-9a68-0db7586d80ad"
$ManagedIdentity = "Tbone-IntuneAutomation"
$Permissions = @(
"DeviceManagementManagedDevices.ReadWrite.All"
"AuditLog.Read.All"
"User.Read.All"
)
#endregion
#region ---------------------------------------------------[Static Variables]------------------------------------------------------
$GraphAppId = "00000003-0000-0000-c000-000000000000" # Don't change this.
#endregion
#region ---------------------------------------------------[Import Modules and Extensions]-----------------------------------------
import-module Microsoft.Graph.Authentication
import-module Microsoft.Graph.Applications
#endregion
#region ---------------------------------------------------[Functions]------------------------------------------------------------
#endregion
#region ---------------------------------------------------[[Script Execution]------------------------------------------------------
Connect-MgGraph -TenantId $TenantId
$IdentityServicePrincipal = Get-MgServicePrincipal -Filter "DisplayName eq '$managedidentity'"
$GraphServicePrincipal = Get-MgServicePrincipal -Filter "appId eq '$GraphAppId'"
$AppRoles = $GraphServicePrincipal.AppRoles | Where-Object {$_.Value -in $Permissions -and $_.AllowedMemberTypes -contains "Application"}
foreach($AppRole in $AppRoles)
{
$AppRoleAssignment = @{
"PrincipalId" = $IdentityServicePrincipal.Id
"ResourceId" = $GraphServicePrincipal.Id
"AppRoleId" = $AppRole.Id
}
New-MgServicePrincipalAppRoleAssignment `
-ServicePrincipalId $AppRoleAssignment.PrincipalId `
-BodyParameter $AppRoleAssignment `
-Verbose
}
#endregion This script can be found on my github on: https://github.com/Mr-Tbone
- Run the script
- Open Enterprise Applications in Entra portal to verify permissions. Make sure to filter on Managed Identities:

Open the app and select permissions

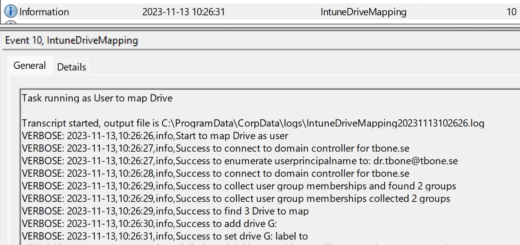
Use the Managed Identity
- Open your Azure Automation Account and select Runbooks
- Click create a runbook, to create a new runbook

- Give the runbook a suitable name and select the type of runbook.

- To start using the managed identity you just need to connect without using any credentials:

I recommend adding the Microsoft Graph modules and use:
Connect-MgGraph -ManagedIdentityNow you can start automating Intune tasks like my script for setting primary user on windows devices: Intune/Intune-Set-PrimaryUsers.ps1 at master · Mr-Tbone/Intune (github.com)